How do hackers or cybersecurity researchers cover their tracks during visiting or scanning any website or any cyber attack? Today, in this article we will discuss an important concept which is proxying. Proxying is a technique bouncing your internet traffic through multiple machines to hide the real identity of your original machine. For achieving this goal we can use a tool which is ProxyChains. So in this article, I am gonna show how to setup proxychains in Kali Linux.
What is ProxyChains?
ProxyChains is open-source software that is available free and most of Linux distro it is pre-installed. If you are using the latest version of Kali Linux it is pre-installed in it. ProxyChains is a tool that redirects the TCP (Transmission Control Protocol) connection with the help of proxies like TOR, HTTP(S), and SOCKS, and it creates a proxy chain server.
When we are using proxychains we can hide our IP address in the real world. In Kali Linux when we are using any tools that time source IP address is our if we are using proxychains that time our IP hide and when we are scanning or visiting any website we give there our IP address as there logs but not the real one.
ProxyChains is very useful, if you are only visiting the website you can use TOR Browser but if you want to hide your whole traffic then you have to use Proxychains.
How to install tor and Proxychains in Kali Linux
First of all, you have to install the Tor services in your Kali Linux. Tor network in the largest anonymous network in the world which is working without any control or in other words Tor network not managed by any organization.
How to install Tor
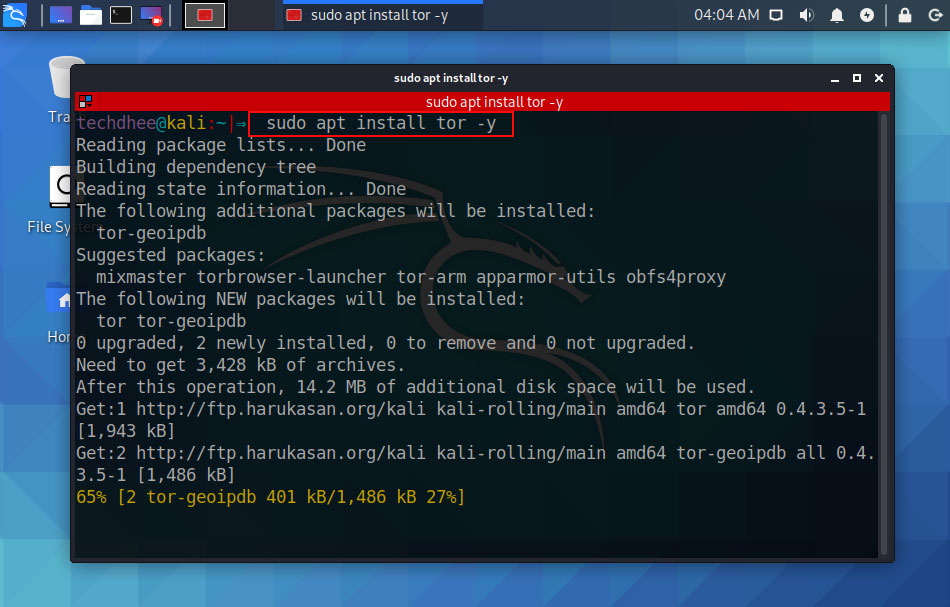
In Kali Linux, we have to install the Tor service, so typing this command you can install the Tor Services in Kali Linux.
techdhee@kali:~|⇒ sudo apt install tor -y
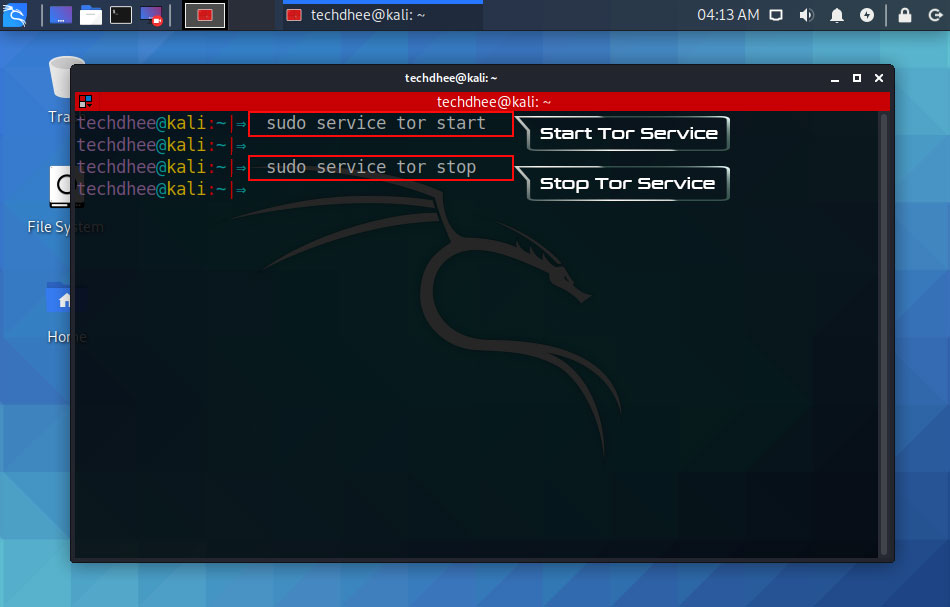
Start/Stop Tor service
How to start/stop the Tor services in Kali Linux. We have to manually start the services or manually stop it after using Tor services.
Start Tor Services
techdhee@kali:~|⇒ sudo service tor start
Stop Tor Services
techdhee@kali:~|⇒ sudo service tor stop
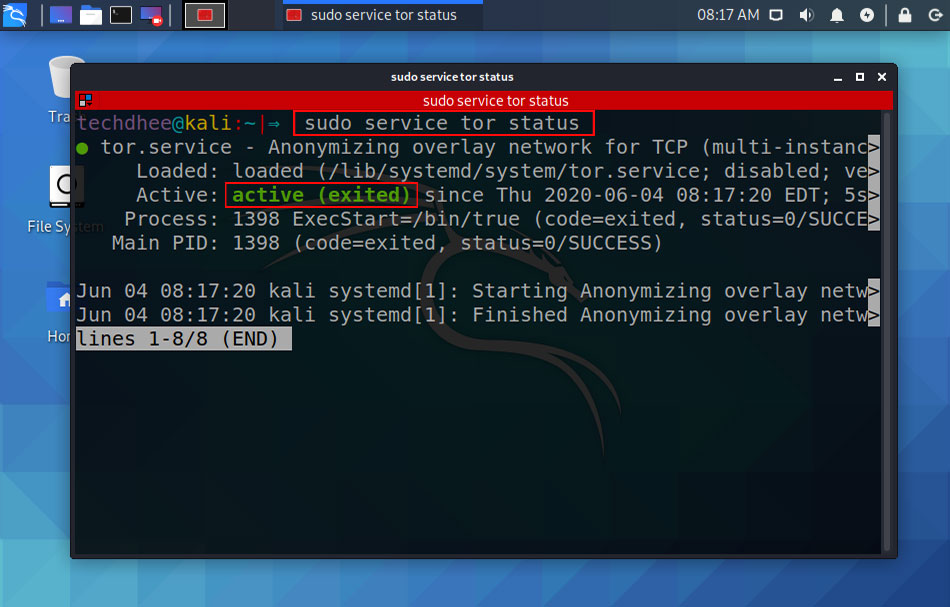
Status of Tor Services
if you need to run proxychains Tor services should be active.
techdhee@kali:~|⇒ sudo service tor status
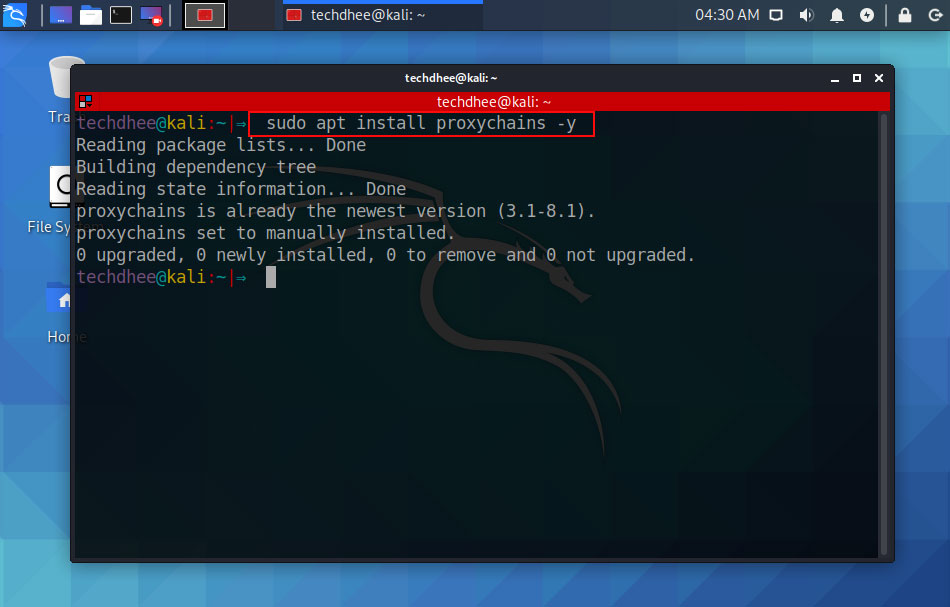
How to install ProxyChains
In the latest version of Kali Linux 2020.2 proxychains comes with pre-installed so we don’t need to install it. Bot if you don’t get this tool in your distro you can install it by typing this command.
techdhee@kali:~|⇒ sudo apt install proxychains -y
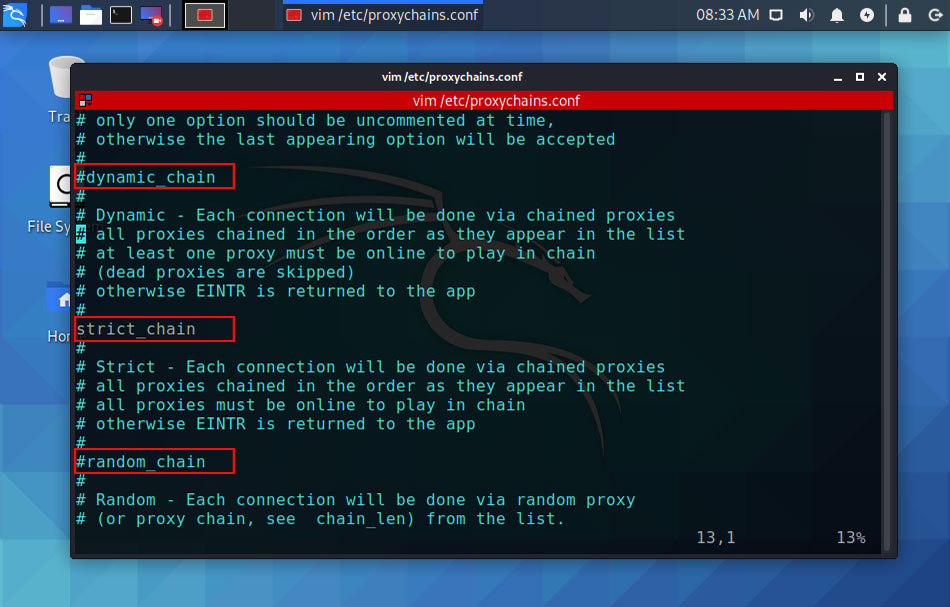
Configuring ProxyChains
Proxychains is fully customizable you can configure with the Tor network as well as proxies like HTTP(S), HTTP, and SOCKS. In proxychains we can choose three different
ProxyChains use three chaining options:
- Strict Chain
- Dynamic Chain
- Random Chain
techdhee@kali:~|⇒ sudo nano /etc/proxychains.conf
Strict Chain
Strict Chain is the default option in proxychains. In this option, every connection goes through the proxies in order that are listed in the configuration file. Strict Chain is very useful when you want your location and you know that your selected proxies working fine. For using a strict chain you have to uncomment “strict_chain” in the configuration file.
Dynamic Chain
Dynamic Chain working the same as a strict chain, it is used all the proxies which are in the configuration file, but it is skipped or excludes those proxies from the chain which is dead or not working at the time. For using a dynamic chain you have to uncomment “dynamic chain” and comment both “random_chain” and “strict_chain” in the configuration file.
Random Chain
Random Chain means randomness which means every connection goes through a proxy which is listed in your configuration file but randomly, no one guesses which proxies are next. For using a dynamic chain you have to uncomment “random_chain” and comment both “dynamic chain” and “strict_chain” in the configuration file.
If you are using random_chain you have to uncomment the “chain_len” line which enables the dynamic chaining. It connects a number of IP addresses in the chain which is randomly generated from your proxies list.
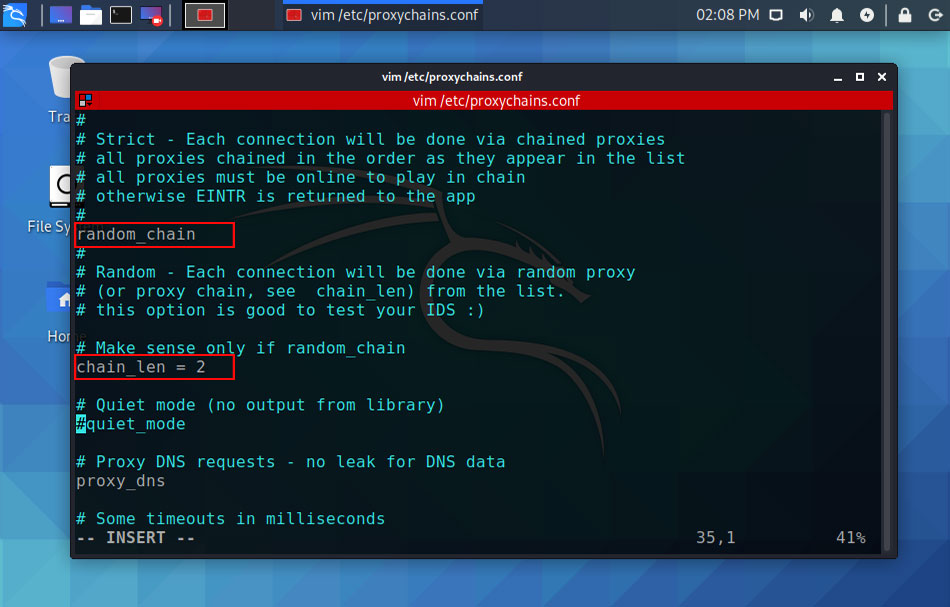
Adding Proxies
To use the proxies in proxychains you have to add the proxies in the configuration file which is located in Kali Linux /etc/proxychains.conf. To open the file you can use your favorite text editor and open it.
techdhee@kali:~|⇒ sudo nano /etc/proxychains.conf
If you go to the end of the file you see there socks4 127.0.0.1 9050, which means default proxychains’s traffic point through our localhost 127.0.0.1 and port 9050. And we all know port 9050 is default Tor port. if you use proxychains using Tor you have to add a line, in the end, config file which is socks5 127.0.0.1 9050.
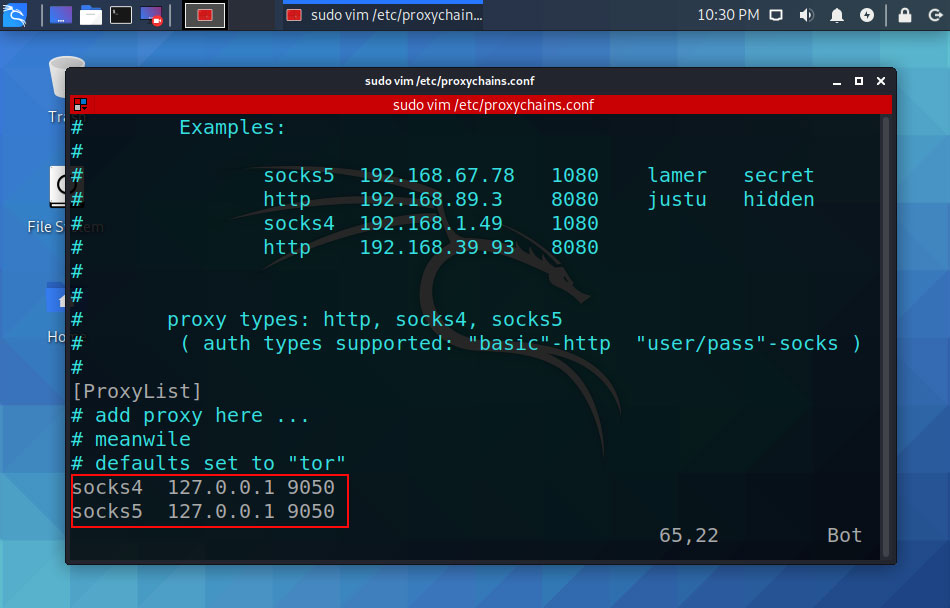
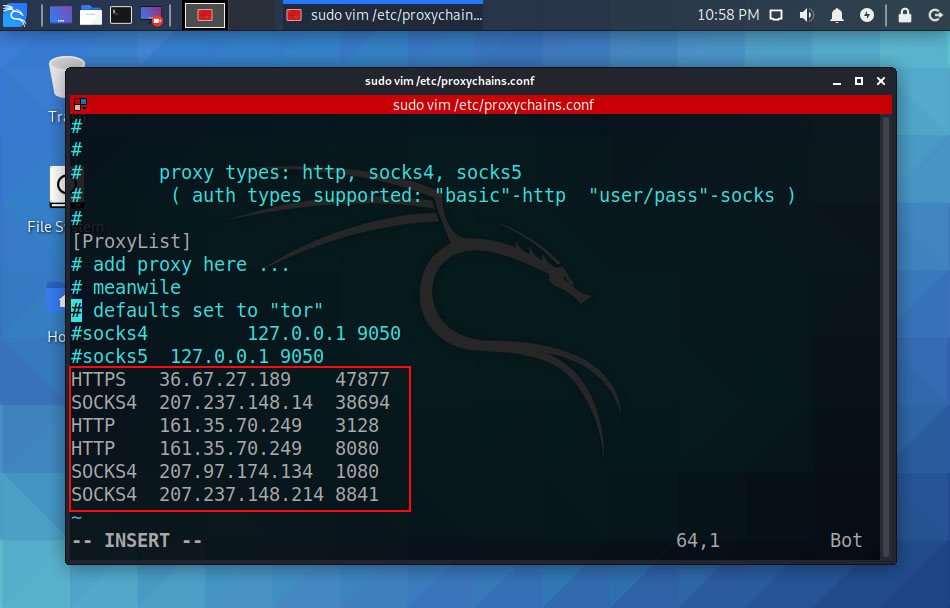
If you do not want to use the Tor network so you have to comment on the socks4 127.0.0.1 9050 line and below that type your proxies list.
Video
In this video, I will show How To Use ProxyChains in Kali Linux Using Tor step by step.
Conclusion
Proxying is an important skill or way if you working in infosec, you have to know about proxying, how to work proxies, and how to get your goal using proxies. ProxyChains is a simple and vastly used tool that helps you to hide your self using proxies. Good luck!
Important Things To Remember:
The author of this article does not promote any illegal activities It is just for education purpose All the activities provided in this article, YouTube channel, and on the website techdhee.in are only for educational purposes.
If you are using and follow this tutorial for any illegal purpose, techdhee.in can not be responsible for your action.
My purpose is to educate or share the information who have not, how to secure your self from the Internet, and the world of digital.
Also, read the Disclaimer
Finally
Thank you for reading this post and keep connected to TECH DHEE to continue enjoying excellent posts. Share your views about this post in the comment section below. If you still have any queries, throw it in the comment section. If you find this post helpful, don’t hesitate to share this post on your social network. It will only take a moment, and also it is quite easy and useful for others.